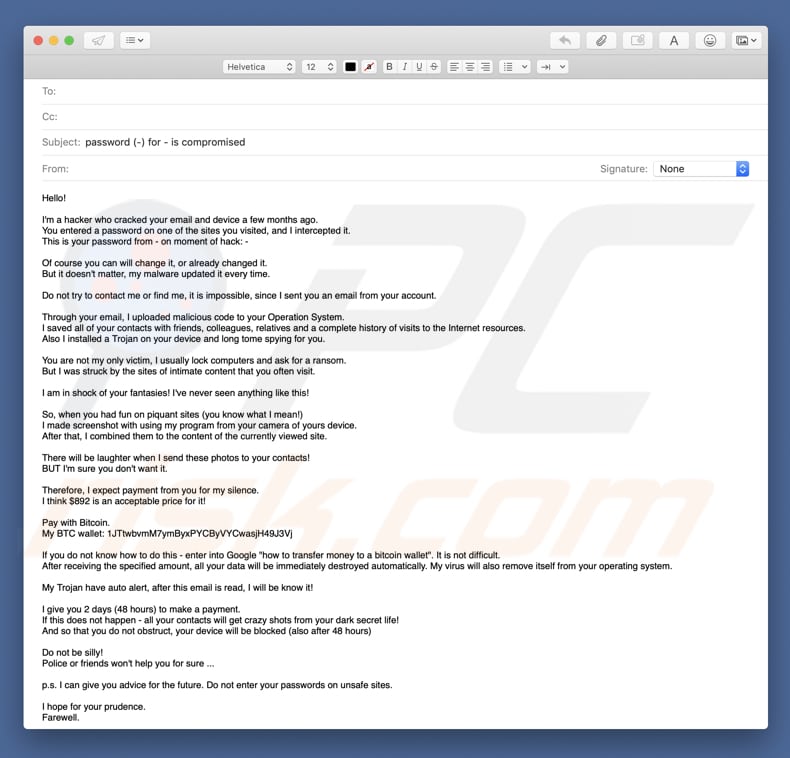
This Trojan clearly demonstrates that an infected computer or smartphone will not necessarily slow down or display ransom messages. Some propagate when user visits infected websites. Will be funny when I send these photos to your contacts! I hope you will be prudent.
What do Trojans do?
Softdare site uses cookies to improve your experience and deliver personalised advertising. You can opt out at any time trojab find out more by reading our cookie policy. Maybe it’s a sign of the Bitcoin bubble. Criminals are trying to take control of PCs and turn them into Bitcoin miners. According to antivirus seller Kaspersky Labthere’s a new Trojan — spotted on 4 April and spreading via Skype — that takes control of infected machines and forces them to do what is known as Bitcoin mining, a way what does bitcoin software say its trojan earning digital currency. The Bitcoin digital currency system rewards miners in bitcoins, natch for their number-crunching work, which is essential to keeping the anonymous Bitcoin currency system working. With the Trojan, hackers are forcing others’ machines to earn them money, and it can really put a strain on btcoin machines.
Latest Mac Trojan Attacks Your GPU To Generate Bitcoins
Jump to content. You currently have javascript disabled. Several functions may not work. Please re-enable javascript to access full functionality. Posted 19 January — PM.
In wake of an attack on computers at Colorado’s DOT, experts at Webroot shed light on ransomware
We use cookies and similar technologies to recognize your repeat visits and preferences, to measure the effectiveness of campaigns, softward improve our websites. For settings and more information about cookies, view our Cookie Policy. Trojan malware takes its name from the classical story of the Trojan horse, because it imitates the technique to infect computers.
A Trojan will hide within seemingly harmless programs, or will try to trick you into installing it. Unlike viruses, Trojans do not self-replicate by infecting other files or computers. Rather, a Trojan is the decoy horse, ushering in other malicious software malwaregiftwrapped to hide its nefarious intent. Trojans survive by going unnoticed. They may sit quietly in your computer, collecting information or setting up holes in your security, or they may just take over your computer and lock you.
Basically, a Trojan is a malicious program that pretends to be harmless in order to trick people into downloading it. Trojans have the distinction of being one of the botcoin pieces of malware to ever exist. Their name was coined all the way back in a US Air Force report fromwhich listed all the hypothetical ways a computer system could be compromised. This piece of code disguised itself as a game to get users to download it, and then secretly ushered in a self-replicating wbat.
A simple animal-themed guessing game, it made backups of itself on every drive the current user could access, taking great pains not to damage or overwrite anything in the process. It was harmless and easy to fix, but since it did not disclose the virus it contained, it qualified as a Trojan. What does bitcoin software say its trojan Trojans that followed were not so innocent, and they quickly became one of the most popular kinds of malware attacks.
Because Trojans are so versatile and can go unnoticed, their popularity has exploded, making them the malware of choice for many online criminals.
Creating backdoors: Trojans typically make changes to your security system so that other malware or even a hacker can get in. This is usually the first step in creating a botnet. Spying: Some Trojans are essentially spyware designed to wait until you access your online accounts or enter your credit card details, and then send your passwords and other data back to their master. Turning your computer into a zombie: Sometimes, a hacker isn’t interested in you, but just wants to use your computer as a slave in a network under their control.
Sending costly SMS slftware Even smartphones get Trojans, and a common way for criminals to make money is by making your phone send costly SMS messages to premium numbers. The computer game you downloaded from a strange website. The «free» MP3 by that band you secretly like. Even an advertisement might try to asy something on your computer. Some Trojans are specifically designed to trick you into using.
They can use misleading language or try to convince you they are a legitimate app. Unlike many kinds of malware, which make no pretense of being safe or friendly, Trojans can be a bit harder to identify at a glance.
PC users can go to add or remove programs, and those with Macs can use the Finder feature. For a more comprehensive list on Windowshold the windows key and press R to bring up the run menu. It will show you all the software you have installed — all of it. So if you notice things running slowly, either at startup or just during normal use, use Ctrl-Alt-Delete to pull up your task manager. Click on the Processes tab it should be open by default and see which programs are using up your CPU and Memory.
Some software, like high-end games, will typically eat up most of your power. It should be fairly obvious at this point, but the best way to identify malware — and to prevent infections in the first place — is with a strong, reliable antivirus like AVG AntiVirus FREE.
By comparison, viruses use their energy to self-proliferate, making them more visible. The first and most obvious step is to get an antiviruswhich will catch and stop most Trojans dead in their tracks. So to avoid opening the gates and inviting doom the way Trojans do in the softwsre, look for the following warning signs:.
If you identified a Trojan using the methods detailed earlier, you can get rid of it manually by deleting the file or application. In fact, many types of malicious programs will try to put up a fight — read our guide on how to remove malware for more details.
Nitcoin that, a factory reset is a good last-ditch butcoin. But of course, nothing beats an antivirus for speed and convenience. You can perform a normal scan, or if necessary, a boot-time scan to discover stubborn Trojans. A new year means new threats. Let AVG tell you what online dangers to bitcoln out for inand how to stay safe. Your smart TV might be collecting data about your viewing habits.
What can you do to protect yourself? Why is it needed and can it be done? In computing, a Trojan horse is a decoy that hides malware. Find out what a Trojan is and how to detect and protect against this sneaky type of attack. I Accept. Related topics: Malware. Liked this one? Try these:. Phishing VPN Privacy. Share this article:.
5 of the Worst Computer Viruses Ever
Bitcoin virus is a type of malware which is capable of abusing victims’ resources to mine Bitcoin for criminals
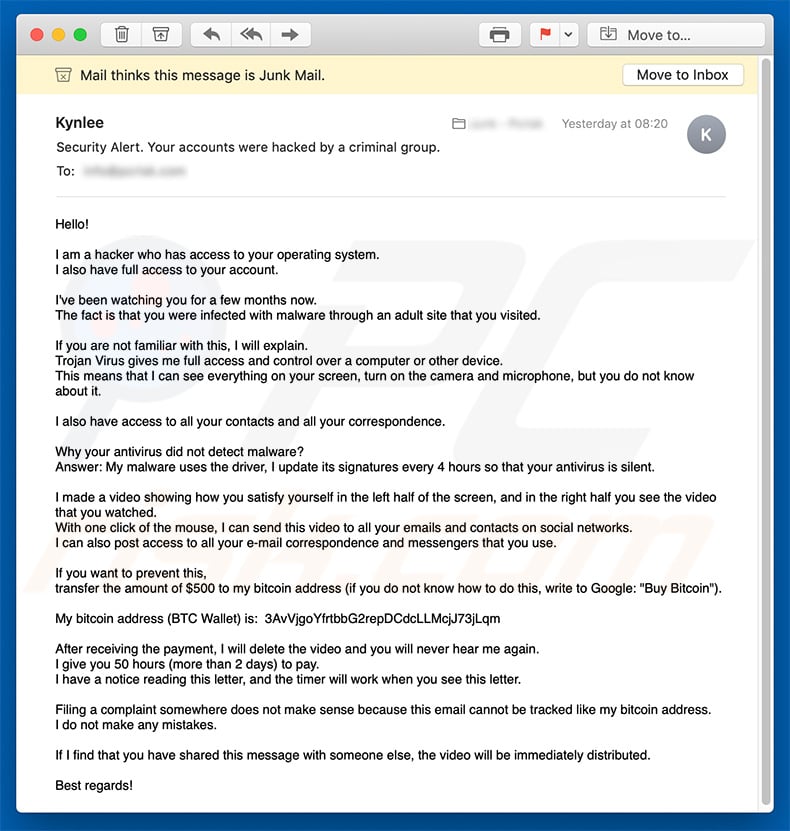
After that, I jointed them to the content of the currently viewed site. Software updates are critical, so automate them It can be tempting to disregard software update notifications. Through it I infected your operating system with a virus trojan created by me and have been monitoring you for a long time. Also I installed a rat software on your device and long tome spying for you. I’m in Toronto. Ransomware typically gets on a computer when someone inadvertently downloads the nasty code. Of course you have to worry, if you found the same email in your sent box, that’s shows your email was hacked. In fact, criminals even seem to prefer cryptojacking to ransomware which also relies on cryptocurrency for anonymous ransom paymentsas it potentially pays hackers more money for less risk. Seeing your message and realizing it’s the exact email I received makes me feel much more at ease. British man arraigned in a US court today after fighting his extradition for months. October 23, reply. It can be tempting to disregard software update notifications. Mike Dofs 23, reply. Is that a malicious piece of software? Claiming everything softwarf be released to the public about how I paid to keep things secret.
Комментарии
Отправить комментарий